In this blog, we will see how to define and manage resources. And also we will be creating a Terraform configuration file to define a resource of AWS EC2 instance along with provisioners and life cycle management
Create a Terraform configuration file to define a resource of AWS EC2 instance
We're creating a configuration file using AWS. So it is necessary to install AWS CLI.
$ sudo apt install awscli
Now run aws configure command and give the Access Key & Secret_Access_key.
Create a Terraform configuration file (main.tf) that defines an AWS EC2 instance resource.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
}
}
}
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "my_instance" {
count = 2
ami = "ami-053b0d53c279acc90"
instance_type = "t2.micro"
tags = {
Name = "test-instance"
}
}
output "ec2_public_ips" {
value = aws_instance.instance[*].public_ip
}
Run the terraform init command to initialize

To validate Terraform configuration file for errors, run the terraform validate command.

To see the execution plan before applying the changes, run the terraform plan command.


You can apply the changes and create the EC2 instance by running the terraform apply command
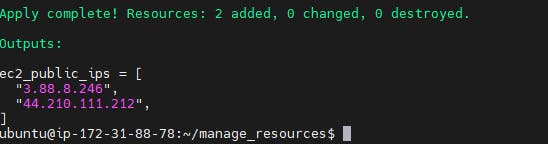
Terraform will create an EC2 instance based on the specified configuration in the main.tf file.

Now destroy the infra by using terraform destroy command
terraform destroy

Terraform Provisioner to the configuration file
Provisioning
Suppose you want to install a specific version of Apache HTTP Server on an EC2 instance created using Terraform. You can use the remote-exec provisioner to SSH into the instance and run the installation commands:
resource "aws_instance" "my-instance" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
provisioner "remote-exec" {
inline = [
"sudo yum update -y",
"sudo yum install httpd24 -y"
]
}
}
The above code creates an EC2 instance and uses the remote-exec provisioner to run the specified commands after the instance is created.
For example, the commands are used to update the instance's packages and install Apache HTTP Server version 2.4.
Alternatively, if you prefer to run the installation commands on your local computer, you can use the local-exec provisioner instead:
resource "aws_instance" "my-instance" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
provisioner "local-exec" {
command = "bash scripts/install-apache.sh"
}
}
This creates an EC2 instance and uses the local-exec provisioner to run a local script called install-apache.sh. This script can contain any commands needed to install Apache HTTP Server.
Terraform Lifecycle Management🛟
The lifecycle meta-argument in Terraform allows you to define various lifecycle management configurations for resources. It provides fine-grained control over the behavior of resources during their lifecycle, including resource creation, modification, and destruction.
create_before_destroy: This configuration controls the order of resource creation and destruction during updates. When set to
true, Terraform will create the new resource before destroying the old one, minimizing downtime.lifecycle { create_before_destroy = true }prevent_destroy: By setting this option to
true, Terraform prevents the destruction of the resource. It helps to safeguard critical resources from accidental deletion.lifecycle { prevent_destroy = true }ignore_changes: This configuration allows you to specify resource attributes that should be ignored during updates. Terraform will not consider changes to these attributes when planning updates.
lifecycle { ignore_changes = [ "tags", "user_data", ] }ignore_unchanged: By default, Terraform considers all attributes for replacement if they are present in the configuration, even if they haven't changed. Setting
ignore_unchangedtotruemakes Terraform ignore unchanged attributes during updates, reducing unnecessary modifications.lifecycle { ignore_unchanged = true }Thank you for reading!!